Overview
What is Graylog?
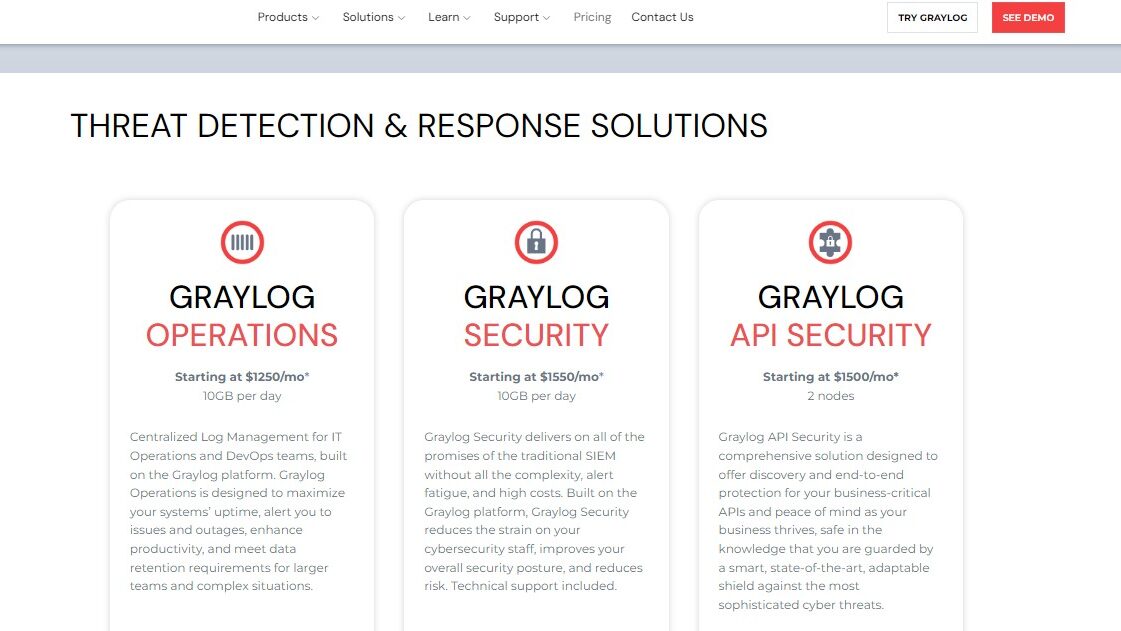
Graylog is a robust log management and analytics platform designed to empower users in searching, visualizing, alerting, and reporting on their log data. With a focus on efficiency and scalability, Graylog provides the tools necessary for handling large volumes of data, making it a valuable asset for organizations seeking comprehensive log analysis solutions.
Why Use Graylog?
- Search: Graylog enables users to build sophisticated queries within minutes, facilitating the search through terabytes of log data in milliseconds. This capability empowers users to ask more questions and obtain quick, actionable answers. Additionally, the platform supports the saving and sharing of searches, promoting collaboration and knowledge-sharing among users.
- Visualize: Users can spot trends and identify anomalies by utilizing a variety of data widgets to customize dashboards tailored to their specific needs. Graylog’s visualization tools allow for a comprehensive understanding of log data, with the ability to quickly drill down into specific details. Saved searches further enhance the visualization experience.
- Alert: The platform provides a powerful alerting system, utilizing triggers, aggregations, and correlations to notify users through various channels such as SMS, Slack, PagerDuty, email, and more. Users can take immediate action based on alerts or initiate custom scripts, showcasing the flexibility and creativity in response to critical events.
- Report: Graylog streamlines the process of automating compliance and management needs. Users can leverage the same widgets used for search results and dashboards to effortlessly build reports. The platform supports the automation of report delivery to any email address, enhancing efficiency in reporting processes.
Who Should Use Graylog?
- IT Administrators: Professionals responsible for managing and analyzing log data to ensure system health, security, and performance.
- DevOps Teams: Individuals involved in continuous monitoring, troubleshooting, and optimization of applications and infrastructure.
- Security Analysts: Professionals focused on identifying and responding to security incidents through log analysis.
Graylog stands out as a comprehensive log management and analytics solution, providing essential tools for searching, visualizing, alerting, and reporting on log data. Whether it’s quickly identifying trends, receiving timely alerts, or automating compliance reports, Graylog offers a versatile and scalable platform for organizations relying on effective log analysis. Explore Graylog to enhance your capabilities in handling and deriving insights from log data efficiently